The use of anti-virus and security software is a prerequisite in most infrastructure scenarios. This makes it all the more important to adapt them to the respective usage scenario. orcharhino as the central hub in the computing cluster is of particular importance.
Not only must the machine itself be uncompromised, but it must also be ensured that the synchronized repositories are malware-free. This article deals with the connection of orcharhino to Sophos Central and configuration of Sophos Antivirus for Linux in relation to orcharhino (tested in versions orcharhino 5.10 and Sophos Antivirus for Linux 1.0.4.3). Sophos Central represents Sophos’s current cloud management platform. The connection of an orcharhino based on CentOS 7 is done easily via the included bootstrap script. In this example, an orcharhino host ‘or30’ is appended:
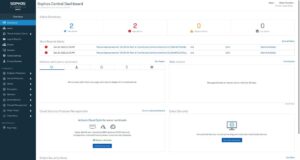
An on-demand scan of the host, i.e. an actively triggered scan, can be started directly from Sophos Central via the ‘Scan’ button. A corresponding output is generated after the scan is completed. In this example, two infected files were detected:
Let’s take a closer look at the findings. Both finds can be found under the directory ‘/var/lib/pulp’. This means files that have been synchronized in an orcharhino repository. Possibly a non-trusted repository was synchronized at the orcharhino. The question now is exactly which files are involved. This is already a much better way of limiting the threat.
The path ‘/var/lib/pulp/content/units/iso’ already reveals that it must be the contents of a Katello file repository. The paths ‘/var/lib/pulp/content/units/rpm’, ‘/var/lib/pulp/content/units/drpm’ and ‘/var/lib/pulp/content/units/deb’ represent rpm, drpm and Debian Content respectively. The Katello repository associated with the infected file can be found out by performing a database query. First, a database login must take place on the orcharhino server:
mongo pulp_database
With the path from the find report the ID of the corresponding file can be identified. In this case, this is the command:
> db.units_iso.find({"_storage_path": {$eq:
"/var/lib/pulp/content/units/iso/fc/006e7d7726b9810ac071a3173fbf583c1b0644098f38082cd23e4adcedb7d7">.pretty()
The output looks like this:
{
"_id" : "2b5c59e8-367a-4f17-9a6e-09ac5e6b9976",
"pulp_user_metadata" : {
},
"_last_updated" : 1639479305,
"_storage_path" : "/var/lib/pulp/content/units/iso/fc/006e7d7726b9810ac071a3173fbf583c1b0644098f38082cd23e4adcedb7d7",
"downloaded" : true,
"name" : "EICAR.sh",
"checksum" : "131f95c51cc819465fa1797f6ccacf9d494aaaff46fa3eac73ae63ffbdfd8267",
"size" : 69,
"_ns" : "units_iso",
"_content_type_id" : "iso"
}
If it is an rpm or a Debian package, the analogous commands ‘units_rpm’ and ‘units_deb’ can be used. In this case, the package name is already included in the filename in clear view. Otherwise, as in this case, the plain name of the corresponding file is returned, here ‘eicar.sh’. The ID under the ‘ID’ field can be used to identify the associated repository:
> db.repo_content_units.find({"unit_id": "2b5c59e8-367a-4f17-9a6e-09ac5e6b9976"}).pretty()
bd9c64b2-b753-4ec0-b316-442472bdc2aa
{
"_id" : ObjectId("61b87809345283bc53b2d192"),
"repo_id" : "a7b580a9-0c34-4864-abfc-4c8fb52c8b18",
"unit_id" : "2b5c59e8-367a-4f17-9a6e-09ac5e6b9976",
"unit_type_id" : "iso",
"updated" : "2021-12-14T10:55:05Z",
"created" : "2021-12-14T10:55:05Z"
}
and thus the actual repository
> db.repos.find({"repo_id" : "a7b580a9-0c34-4864-abfc-4c8fb52c8b18"}).pretty()
{
“_id” : ObjectId(“61b8632a2c07265c65c9a543”),
“repo_id” : “a7b580a9-0c34-4864-abfc-4c8fb52c8b18”,
“display_name” : “Sophos-EICAR”,
“notes” : {
},
“scratchpad” : {
},
“_ns” : “repos”,
“last_unit_added” : ISODate(“2021-12-14T10:55:05.250Z”),
“last_unit_removed” : ISODate(“2021-12-14T10:53:39.751Z”),
“content_unit_counts” : {
“iso” : 1
}
}
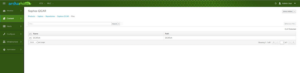
A look into the corresponding repository “Sophos-EICAR” via the orcharhino GUI shows the file in question:
If you want to exclude the repositories from a scan (e.g. if the repository contents are already checked at a proxy during download), the directory /var/lib/pulp can be excluded from the scan via the policy.
It should be noted that when a repository is published under a content view, soft links can be found under var/lib/pulp/published to the individual contents of the repository. These can be followed to the actual files.
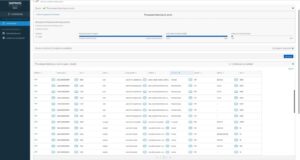
Sophos offers another tool that is helpful for monitoring orcharhino: ‘Live Discovery’. Sophos Central’s Live Discovery feature can help check the health of the orcharhino server. For example, the processes with open ports can be listed to verify the corresponding orcharhino services:
Please note:
- These are some examples of how, you can improve the monitoring of an orcharhino. This article does not aim to cover all facets of server monitoring. Especially for on-access scans, performance and integrity must be considered when using the orcharhino database services.
- Mongo will be replaced as backend for pulp with the next major orcharhino version 6.
Martin Grundei
Latest posts by Martin Grundei (see all)
- orcharhino and Sophos – a malware trail search - 11. February 2022